Wednesday, September 24, 2008
Google Privacy Vulnerability May Share Your Full Name, and How Google Might Help Phishers
Be careful when you want to share your Gmail email address but not your name. If you signed up for Google’s mail app with your real name, people knowing certain privacy holes in Google’s applications will be able to find out your first and last name as you provided them. E.g. if your email address is “ExampleElven2000@gmail.com” and you pass it on, someone could take this address, apply the trick, and end up with the full name “Jane Doe”, even if you never contacted them in any way.
One multi-step approach to find out the name was posted to a security blog recently. Also, some of us forwarded one way to go from email nick to full name in a different, quicker way to Google security over two months ago – it’s an approach where one can utilize the Google Apps program – but nothing got fixed (there also wasn’t a human response, just the automated reply).
To some people, the sharing of a full name is no big deal, or they might not have entered their real name in the first place when signing up with Google, or maybe their email address already contains their full name (like “janedoe@gmail.com”). Others however may figure they’re staying anonymous when using nicks like “ExampleElven2000” or whatever was picked.
How Google builds tools that could help phishers
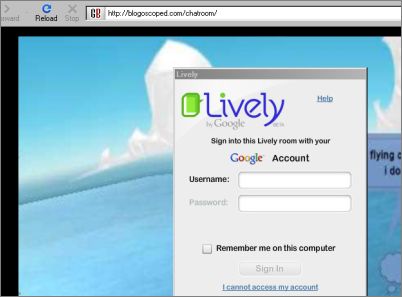
Entering your Google password at a non-google.com URL should usually be avoided.
On the note of security, Google is also kind of helping phishers find easier prey; parts of some of their tools, like Google Lively and more recently Google Chrome, train people to not look at the URL when entering their account credentials. For instance, the Lively 3D chat widget can be embedded into any page and will ask for your password without a visible forward to google.com – so anyone could fake most parts of the application asking for your credentials (I alerted Google to this on July 9th though the issue persists). And once an attacker got the Google Account credentials, they can do things like reading your email, creating AdWords campaigns under your name, read your Google Docs files and so on, depending on what tools you’re using with Google.
In Google Chrome on the other hand, a special mode allows users to put a website into a pseudo desktop application mode... a mode in which the URL won’t be shown anymore, making it easier to fake a website to fish for user credentials. Let’s say you’re putting application FriendlyApp into the desktop mode and open it next time, and after receiving an email or other message in FriendlyApp you’re asked to re-enter your FriendlyApp password to continue; how would you tell if you’re truly still on friendlyapp.com, or whether someone tricked you onto an external site trying to grab your password? This won’t work with just any friendly application (e.g. an application may open all external links in new windows) but it creates an unnecessary risk for many other apps.
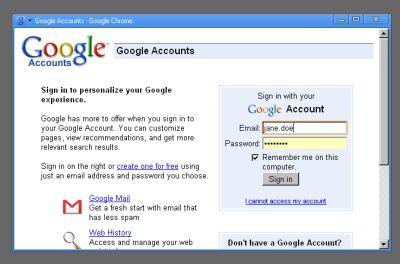
This is all a Chrome desktop app will show you – do you know at which domain you’re currently entering your Google password?
[Thanks Juha-Matti Laurio! Hat tip to Garett and Tony.]
>> More posts
Advertisement
This site unofficially covers Google™ and more with some rights reserved. Join our forum!
